ABOUT
Our cybersecurity laboratory aims to conduct research toward a cyber society that allows anyone to feel safe in using the Internet. To achieve this, we focus on the key components of cyberspace – computers, network systems, and end users.
OVERVIEW
As the Internet has become a part of the infrastructure of our society, cyber society has become tightly connected to our daily lives. This, however parallels with an increase in cyber threats. Understanding that all cyber threats cannot be solved, we are working on practical research to improve the security of the cyber society, while considering the aversion and acceptance of risk.
Our lab approaches cyber threats from three perspectives: technical, human, and organizational. From a technical perspective, we are studying malware countermeasures, honeypot technologies, DoS / DDoS countermeasures, traffic analysis, cyber range technologies, and cyber physical security technologies. Human factors cover phishing site countermeasures, targeted email countermeasures, situational awareness in security, and decision-making theory. Organizational approaches look at incident response and organizational cooperation, automated threat analysis, security education, and international standardization activities, etc. Our research targets not only these keywords, but also all of the elements that make up cyberspace.
RESEARCH AREAS
1. Anti-phishing technology
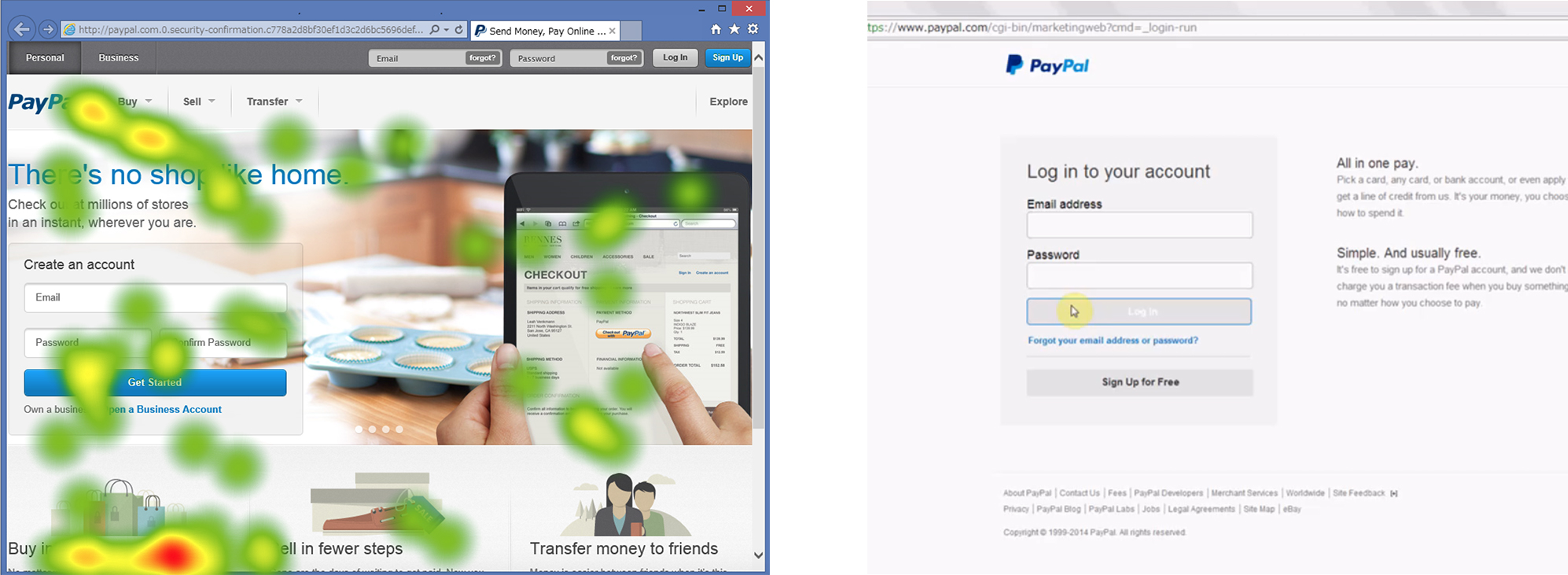
Phishing is a cyber threat that tricks end users to exploit personal information by disguising legitimate emails and websites. Users are required to find security information and make very difficult judgements on mail and site content that has been very cleverly disguised. We are conducting research focusing on user behaviour, in particular the way users browse information, to analyze what the user refers to in making decisions.
The figure above left shows the eye movement of a user who is viewing content without paying attention to security information. The figure on the right introduces a browser extension development that tracks the user’s gaze and does not accept personal information until the user confirms the site security information.
2. Multi-layer threat protection
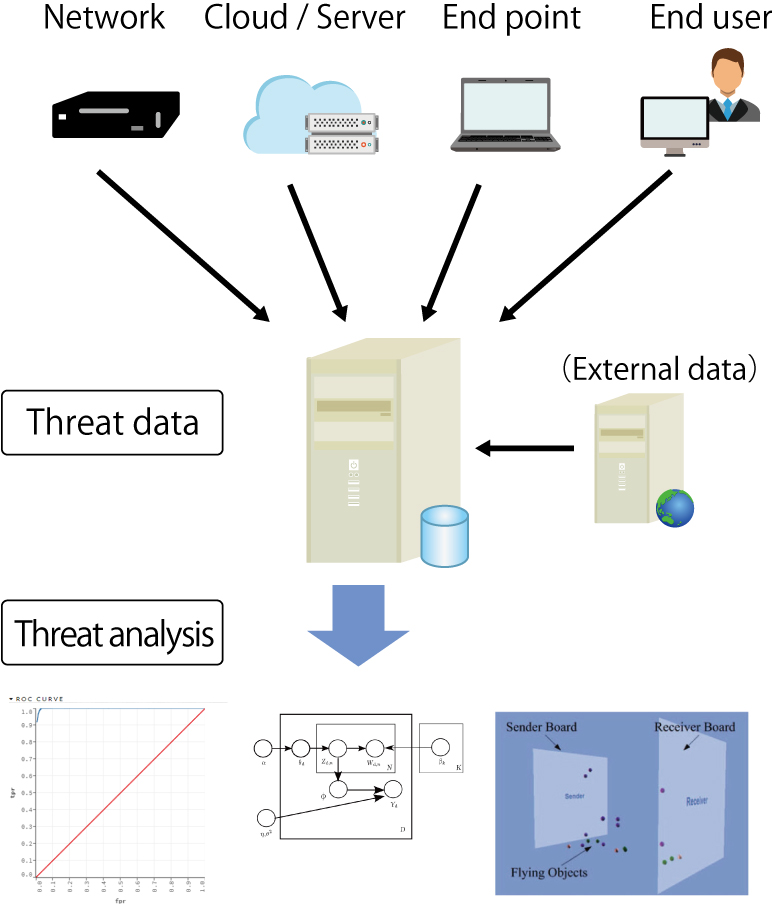
In addition to tracking user behaviour, rapid detection of signs of targeted attacks from changes in trends viewed through the collection of cyber threat data such as malware and unauthorized access is essential. From an early stage, our lab has employed machine learning in working on cyber threat data analysis and is currently developing a practical countermeasure system. Multi-layer threat protection measures involve an understanding of network infrastructure technologies, system operation, cyber threat data analysis, and the ability to take effective security measures. Toward this goal, we are working in cooperation with domestic and international researchers.
The figure illustrates the concept of collecting and analyzing cyber threat data from a high level view. Research topics for the system include the development of a data analysis platform and exploratory data analysis. For end users, we are designing training exercises and developing educational content.
RESEARCHER

Daisuke Miyamoto
Associate Professor
Department of Information and Communication Engineering, Graduate School of Information Science and Technology, the University of Tokyo
Born in 1977. After completing the master’s program at Nara Institute of Science and Technology (NAIST), Daisuke gained experience as a network engineer before returning to NAIST to complete his doctoral degree and proceed to a career in research.
PROFILE
Education
| April 1996 – March 2000 | Kansei Gakuin University, Faculty of Commerce |
|---|---|
| April 2000 – March 2002 | Master’s Course, Graduate School of Information Science and Technology, Nara Institute of Science and Technology |
| April 2005 – March 2008 | Doctoral Program, Graduate School of Information Science and Technology, Nara Institute of Science and Technology |
| March 2009 | Ph.D. (Engineering) |
Professional Background
| April 2002 – March 2005 | Network Division, Accelia, Inc. (Engineer) |
|---|---|
| April 2008 – March 2009 | Graduate School of Science and Technology, Nara Institute of Science and Technology (Researcher) |
| April 2009 – March 2011 | National Institute of Information and Communications Technology (Expert Researcher) |
| April 2011 – March 2017 | Information Technology Center, The University of Tokyo (Assistant Professor) |
| April 2017 – September 2018 | Graduate School of Information Science and Technology, Nara Institute of Science and Technology (Project Associate Professor) |
| October 2018 – | present Graduate School of Information Science and Technology, The University of Tokyo (Associate Professor) |
MEMBERS
Laboratory
| Yuki Yagi | M2, Guraduate School of Information Science and Technology |
|---|---|
| Naoya Tezuka | M1, Guraduate School of Information Science and Technology |
| Chaoran Yang | M1, Guraduate School of Information Science and Technology |
Researcher
| Magnus Krumbacher | Guraduate School of Information Science and Technology |
|---|
Alumni
| Shinji Yamazaki | 2020/4~2022/3 |
|---|---|
| Lin Leo | 2021/4~2023/3 |
Past researcher
| Masahide Yumura | 2020/4~2022/3 |
|---|